- Tone2 Filterbank3 Keygen For Mac Windows 7
- Tone2 Filterbank3 Keygen For Mac Windows 10
- Tone2 Filterbank3 Keygen For Mac Os
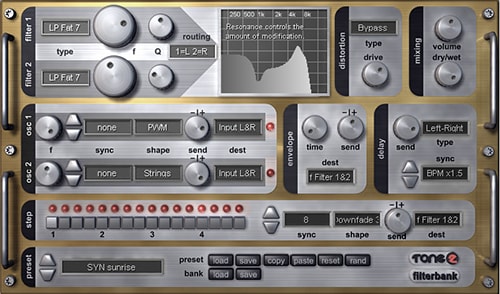
- FilterBank3 Tone2 FilterBank is more than an analog-modeled filter plugin: It is a synthesizer AND a flexible multi-effect unit. The modular design and flexible modulation-routing offer a wide range of possibilities. With a huge amount of filters, oscillators and feedback you can create complete sequences and textures.
- Windows / Mac FilterBank3 Tone2 FilterBank is more than an analog modeled filter plugin - it is a synthesizer AND a flexible multi-effect unit. The modular design and flexible modulation routing give you almost unlimited possibilities.
- Tone2 FilterBank3 v3.4.0-R2R Team R2R Jan 11 2020 3.12 MB Tone2 FilterBank is more than an analog modeled filter plugin - it is a synthesizer AND a flexible multi-effect unit. The modular design and flexible modulation routing give you almost unlimited possibilities.
- This software is compatible with Mac and Windows platforms, and can operate in standalone mode (Windows only), as well as within AU and VSTi formats. Tone2 – Gladiator 2 – a powerful virtual synthesizer deserving special attention. This tool, perhaps, is the best among tools of this size.
Tone2 FilterBank3 upgrade is a Graphic Apps::Multimedia software developed by Tone2 Audiosoftware. After our trial and test, the software was found to be official, secure and free. Here is the official description for Tone2 FilterBank3 upgrade: FilterBank3
Tone2 FilterBank3 is more than a filter plugin - it is a complete VST synthesizer and a flexible multi-effect unit. The modular design and flexible modulation routing give you nearly unlimited possibilities. With self-oscillating filters, oscillators and feedback it can create complete sequences and textures. FilterBank sounds are impressive and absolutely unique. The built-in step sequencer can create rhythmic sequences with some mouse clicks.
* 58 high-end stereo filters
* semi - modular architecture
* flexible routing
* 2 anti-aliased OSCs/LFOs with BPM Sync and 11 wave shapes
* alias free FM and AM
* 12 over sampled types of distortion
* 20 types of surround delay, reverb
* 318 presets
* can be loaded as synthesizer as well as effect
* vocal filtering, equalizing, phasing, flanging, compression
* feedback
* step sequencer
* Midi learn
* autosync to BPM
* realtime frequency display
* envelope follower
* Tool tips and help functions
* VST 2.4 / AU, stereo, 64 Bit accuracy
..
Tone2 - FilterBank v3.4 (Mac OS X) 11 Mb Tone2 FilterBank is more than an analog modeled filter plugin - it is a synthesizer AND a flexible multi-effect unit. The modular design and flexible modulation routing give you almost unlimited possibilities.
FilterBank3
Tone2 FilterBank3 is more than a filter plugin - it is a complete VST synthesizer and a flexible multi-effect unit. The modular design and flexible modulation routing give you nearly unlimited possibilities. With self-oscillating filters, oscillators and feedback it can create complete sequences and textures. FilterBank sounds are impressive and absolutely unique. The built-in step sequencer can create rhythmic sequences with some mouse clicks.
* 58 high-end stereo filters
* semi - modular architecture
* flexible routing

* 2 anti-aliased OSCs/LFOs with BPM Sync and 11 wave shapes
* alias free FM and AM
* 12 over sampled types of distortion
* 20 types of surround delay, reverb
* 318 presets
* can be loaded as synthesizer as well as effect
* vocal filtering, equalizing, phasing, flanging, compression
* feedback
* step sequencer
* Midi learn
 * autosync to BPM
* autosync to BPM* realtime frequency display
* envelope follower
* Tool tips and help functions
* VST 2.4 / AU, stereo, 64 Bit accuracy
you can download Tone2 FilterBank3 upgrade free now.
Apr 16, 2019 Cisco NAC Appliance, formerly known as Cisco Clean Access, is a network admission control (NAC) system developed by Cisco Systems designed to produce a secure and clean network environment. Baseline Network Admission Control based on users, ports, and MAC addresses Easy network configuration, Cisco IOS Software updates, and troubleshooting using Cisco Network Assistant software Auto-configuration using Smartports Enhanced troubleshooting for link. Baseline Network Admission Control based on users, ports, and MAC addresses Easy network configuration, Cisco IOS Software updates, and troubleshooting using Cisco Network Assistant software QoS for traffic classification and shaping to prioritize various applications. The Cisco AnyConnect VPN (Virtual Private Network) Client allows you to make secure connections to UNC servers from off-campus. Be Aware of Export Controls If you plan to take the Cisco VPN out of the country on a computer or plan to download it while abroad, be aware that the US Department of Commerce restricts the export of cryptographic. Cisco NAC Agent The Cisco NAC Agent, also referred to as the Clean Access Agent or Software Agent, is a Cisco-provided, free software program that resides on client PCs. Its purpose is to gather information about the user and device on which it is installed. It runs on a variety of endpoint machines (Windows, Mac) and is provisioned over the web.
Network Access Control (NAC) is an approach to computer security that attempts to unify endpoint security technology (such as antivirus, host intrusion prevention, and vulnerability assessment), user or system authentication and network security enforcement.[1][2]
Description[edit]
Network Access Control (NAC) is a computernetworking solution that uses a set of protocols to define and implement a policy that describes how to secure access to network nodes by devices when they initially attempt to access the network.[citation needed] NAC might integrate the automatic remediation process (fixing non-compliant nodes before allowing access) into the network systems, allowing the network infrastructure such as routers, switches and firewalls to work together with back office servers and end user computing equipment to ensure the information system is operating securely before interoperability is allowed. A basic form of NAC is the 802.1X standard.
Network Access Control aims to do exactly what the name implies—control access to a network with policies, including pre-admission endpoint security policy checks and post-admission controls over where users and devices can go on a network and what they can do. Dbx viewer for mac.
Example[edit]
When a computer connects to a computer network, it is not permitted to access anything unless it complies with a business defined policy; including anti-virus protection level, system update level and configuration. While the computer is being checked by a pre-installed software agent, it can only access resources that can remediate (resolve or update) any issues. Once the policy is met, the computer is able to access network resources and the Internet, within the policies defined by the NAC system. 2018 kawasaki z1000 repair manual. NAC is mainly used for endpoint health checks, but it is often tied to Role-based Access. Access to the network will be given according to the profile of the person and the results of a posture/health check. For example, in an enterprise the HR department could access only HR department files if both the role and the endpoint meets anti-virus minimums.
Goals of NAC[edit]
Because NAC represents an emerging category of security products its definition is both evolving and controversial. The overarching goals of the concept can be distilled as:
- Mitigation of zero-day attacks
- Authorization, Authentication and Accounting of network connections.
- Encryption of traffic to the wireless and wired network using protocols for 802.1X such as EAP-TLS, EAP-PEAP or EAP-MSCHAP.
- Role-based controls of user, device, application or security posture post authentication.
- Automation with other tools to define network role based on other information such as known vulnerabilities, jailbreak status etc.
- The main benefit of NAC solutions is to prevent end-stations that lack antivirus, patches, or host intrusion prevention software from accessing the network and placing other computers at risk of cross-contamination of computer worms.
- Policy enforcement
- NAC solutions allow network operators to define policies, such as the types of computers or roles of users allowed to access areas of the network, and enforce them in switches, routers, and network middleboxes.
- Identity and access management
- Where conventional IP networks enforce access policies in terms of IP addresses, NAC environments attempt to do so based on authenticated user identities, at least for user end-stations such as laptops and desktop computers.
Concepts[edit]
Pre-admission and post-admission[edit]
There are two prevailing designs in NAC, based on whether policies are enforced before or after end-stations gain access to the network. In the former case, called pre-admission NAC, end-stations are inspected prior to being allowed on the network. A typical use case of pre-admission NAC would be to prevent clients with out-of-date antivirus signatures from talking to sensitive servers. Alternatively, post-admission NAC makes enforcement decisions based on user actions, after those users have been provided with access to the network
Agent versus agentless[edit]
The fundamental idea behind NAC is to allow the network to make access control decisions based on intelligence about end-systems, so the manner in which the network is informed about end-systems is a key design decision. A key difference among NAC systems is whether they require agent software to report end-system characteristics, or whether they use scanning and network inventory techniques to discern those characteristics remotely.
As NAC has matured, software developers such as Microsoft have adopted the approach, providing their network access protection (NAP) agent as part of their Windows 7, Vista and XP releases. There are also NAP compatible agents for Linux and Mac OS X that provide equal intelligence for these operating systems.
Out-of-band versus inline[edit]
In some out-of-band systems, agents are distributed on end-stations and report information to a central console, which in turn can control switches to enforce policy. In contrast the inline solutions can be single-box solutions which act as internal firewalls for access-layer networks and enforce the policy. Out-of-band solutions have the advantage of reusing existing infrastructure; inline products can be easier to deploy on new networks, and may provide more advanced network enforcement capabilities, because they are directly in control of individual packets on the wire. However, there are products that are agentless, and have both the inherent advantages of easier, less risky out-of-band deployment, but use techniques to provide inline effectiveness for non-compliant devices, where enforcement is required.
Remediation, quarantine and captive portals[edit]
Tone2 Filterbank3 Keygen For Mac Windows 7
Network operators deploy NAC products with the expectation that some legitimate clients will be denied access to the network (if users never had out-of-date patch levels, NAC would be unnecessary). Because of this, NAC solutions require a mechanism to remediate the end-user problems that deny them access.
Two common strategies for remediation are quarantine networks and captive portals:
- Quarantine
- A quarantine network is a restricted IP network that provides users with routed access only to certain hosts and applications. Quarantine is often implemented in terms of VLAN assignment; when a NAC product determines that an end-user is out-of-date, their switch port is assigned to a VLAN that is routed only to patch and update servers, not to the rest of the network. Other solutions use Address Management techniques (such as Address Resolution Protocol (ARP) or Neighbor Discovery Protocol (NDP)) for quarantine, avoiding the overhead of managing quarantine VLANs.
- Captive portals
- A captive portal intercepts HTTP access to web pages, redirecting users to a web application that provides instructions and tools for updating their computer. Until their computer passes automated inspection, no network usage besides the captive portal is allowed. This is similar to the way paid wireless access works at public access points.
- External Captive Portals allow organizations to offload wireless controllers and switches from hosting web portals. A single external portal hosted by a NAC appliance for wireless and wired authentication eliminates the need to create multiple portals, and consolidates policy management processes.
Tone2 Filterbank3 Keygen For Mac Windows 10
Mobile NAC[edit]
Using NAC in a mobile deployment, where workers connect over various wireless networks throughout the workday, involves challenges that are not present in a wired LAN environment. When a user is denied access because of a security concern, productive use of the device is lost, which can impact the ability to complete a job or serve a customer. In addition, automated remediation that takes only seconds on a wired connection may take minutes over a slower wireless data connection, bogging down the device.[3] A mobile NAC solution gives system administrators greater control over whether, when and how to remediate the security concern.[4] A lower-grade concern such as out-of-date antivirus signatures may result in a simple warning to the user, while more serious issues may result in quarantining the device.[5] Policies may be set so that automated remediation, such as pushing out and applying security patches and updates, is withheld until the device is connected over a Wi-Fi or faster connection, or after working hours.[3] This allows administrators to most appropriately balance the need for security against the goal of keeping workers productive.[5]
Cisco Network Admission Control Agent Software For Mac Windows 7
Tone2 Filterbank3 Keygen For Mac Os
See also[edit]
Cisco Network Admission Control Agent Software For Mac Download
References[edit]
- ^'IEEE 802.1: 802.1X-REV – Revision of 802.1X-2004 – Port Based Network Access Control'. ieee802.org.
- ^Tutorial: Network Access Control (NAC) Mike Fratto, Network Computing, July 17, 2007
- ^ ab'Mobile Network Access control: Extending Corporate Security Policies to Mobile Devices'(PDF). Archived from the original on October 5, 2011. Retrieved 2011-05-28.CS1 maint: BOT: original-url status unknown (link)
- ^'Network Access Control Module'Archived 2011-09-03 at the Wayback Machine
- ^ ab'Field Technologies Online'. Archived from the original on March 14, 2012. Retrieved 2011-05-28.CS1 maint: BOT: original-url status unknown (link)
External links[edit]
Cisco Network Admission Control Agent Software For Mac 2017

Comments are closed.